Understanding Mach IPC and Injection Techniques
This document is still a draft. Please note that there might be mistakes or inaccuracies.
Inter Process Communication (IPC) and code injection are essential techniques in the field of system security and software exploitation. This article explores various aspects of Mach IPC and injection techniques, including practical examples and case studies.
Table of Contents
- Mach Inter Process Communication (IPC) Concepts
- Injection via Mach Task Ports
- BlockBlock Case Study - Injecting execv Shellcode
- Injecting a Dylib
Mach Inter Process Communication (IPC) Concepts
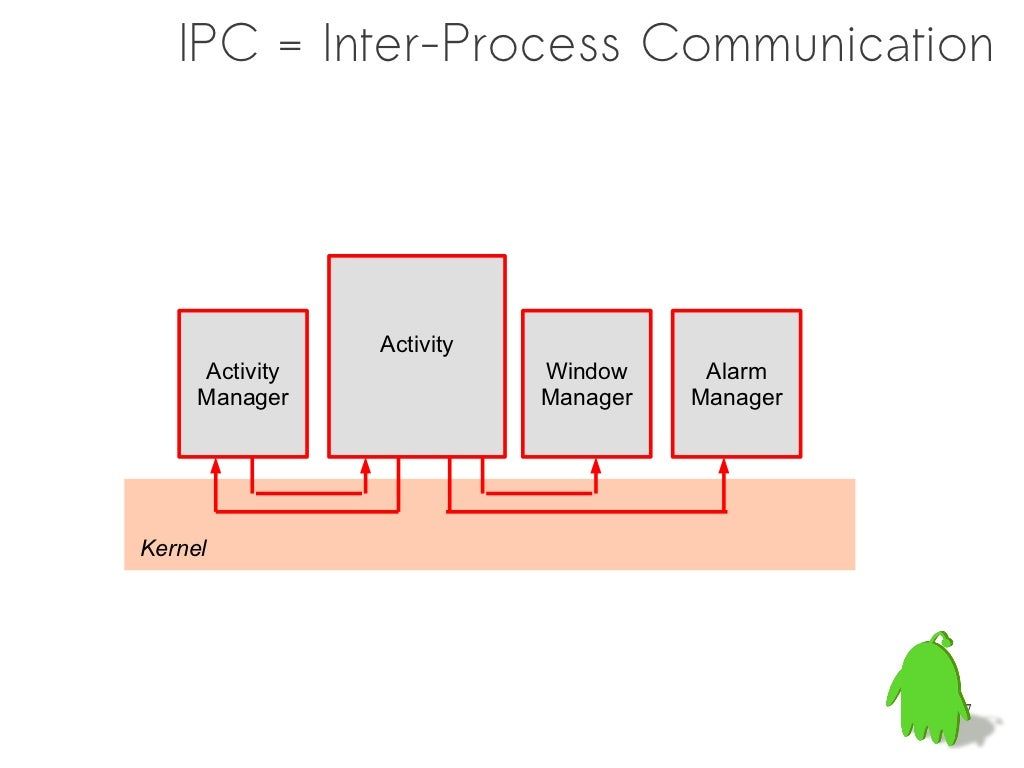
Mach IPC is a fundamental mechanism in macOS that allows processes to communicate and share resources. This section provides an overview of key Mach IPC concepts.
Injection via Mach Task Ports
Learn how Mach task ports can be exploited for code injection, including the process of acquiring the SEND right, writing to remote process memory, and starting a remote thread.
Getting the SEND Right
Discover the importance of obtaining the SEND right for a Mach task port and its role in injection techniques.
In the realm of Mach Inter-Process Communication (IPC), understanding the intricacies of rights and capabilities is fundamental. One of the most crucial rights to grasp is the SEND right for a Mach task port. Obtaining the SEND right is a critical step in various code injection techniques, and it plays a pivotal role in manipulating and interacting with other processes.
The Importance of the SEND Right
The SEND right grants the holder the ability to send messages to the target Mach port. In the context of code injection, this right enables a process to communicate with another process and exert control over it. This control can range from injecting code and data into the target process’s address space to manipulating its execution.
In essence, the SEND right is the gateway to performing tasks that would otherwise be restricted or inaccessible. It allows an attacker or researcher to influence the behavior of the target process, making it a coveted and powerful capability.
Its Role in Injection Techniques
When it comes to code injection techniques, such as DLL (Dylib) injection or thread creation, obtaining the SEND right is often the first step. Without this right, the process attempting to inject code or manipulate another process’s behavior is severely limited.
By acquiring the SEND right for a Mach task port, an attacker can establish a communication channel with the target process, enabling the transfer of code and data. This communication is the foundation for various injection methods, including writing to remote process memory and initiating the execution of injected code within the target process.
Writing to Remote Process Memory
Explore the process of injecting code by writing to the memory space of a remote process.
Starting a Remote Thread
Learn how to initiate the execution of injected code by starting a remote thread within the target process.
BlockBlock Case Study - Injecting execv Shellcode
Delve into a real-world case study involving the BlockBlock application, focusing on injecting execv shellcode.
The Vulnerability
Understand the vulnerability in BlockBlock that allows for code injection.
The BlockBlock Shellcode
Examine the execv shellcode used to inject and execute code within the BlockBlock process.
Finding the Process ID
Learn how to identify the target process’s ID for injection.
Putting it Together
Walk through the complete process of injecting and executing code within the BlockBlock process.
Injecting a Dylib
Explore the process of injecting dynamic libraries (dylibs) into macOS processes.
Promoting Mach Thread to POSIX Thread
Understand how to promote a Mach thread to a POSIX thread, a crucial step in dylib injection.
The Shellcode
Examine the shellcode used to inject a dylib into a target process and initiate its execution.
This comprehensive article provides insights into the intricacies of Mach IPC and code injection, offering practical knowledge and case studies for security researchers and developers alike.